Categories
Cyber Breach Analysis Related Products
Do hackers know me?
See yourself through the eyes of a hacker
Data Breach Analysis

Cyber Pulse
Stay ahead of cyber threats with AI-powered intelligence.
Ransomware Intelligence

Exploit Alarm
Vulnerability intelligence for real-time threat analysis
Threat Intelligence
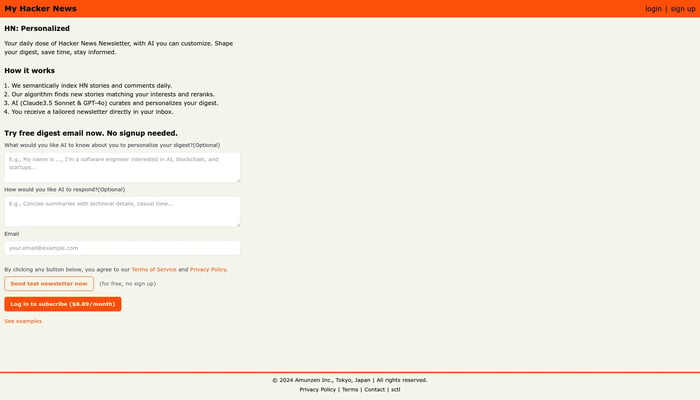
My Hacker News
Your daily dose of personalized Hacker News Newsletter.
Personalized News Digest

Palitronica Inc
Detect cyber attacks on critical physical infrastructure
Side-Channel Analysis
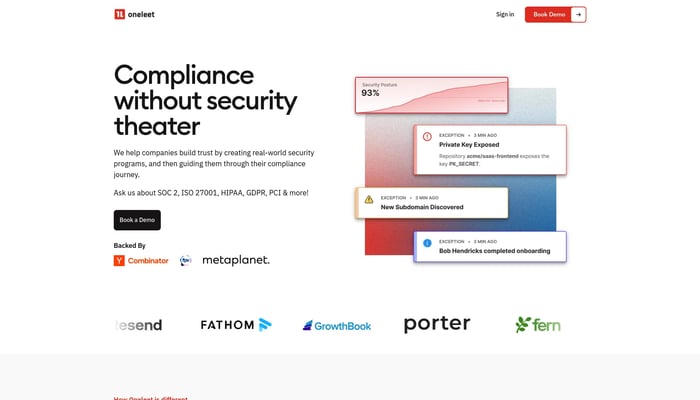

Oneleet
Automated security and compliance without security theater
Vulnerability Management
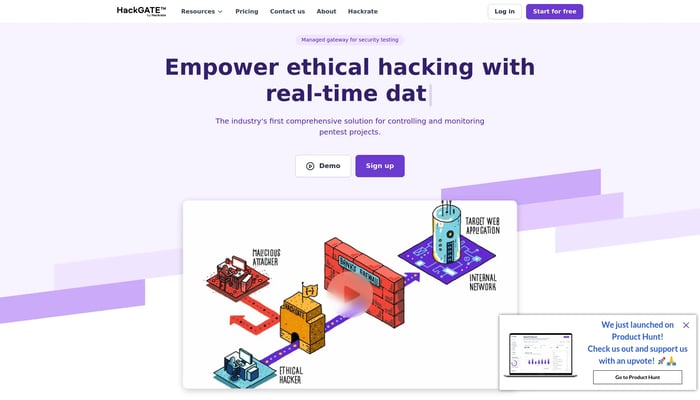

HackGATE
Empowering ethical hacking with visibility and control
Penetration Testing
CyberFend
Cyberfend delivers robust, real-time web and mobile security by…
Fraud Detection

Cyble
Cyble is one of the fastest-growing threat intelligence provider.
Data Analysis

Overwatch
Enterprise software for strategic, risk, and cyber fraud intelligence
Fraud Detection

Remy
Resolve product security risks early with AI
AI-Powered Security

Stacksi
Automated Answers to Security Questionnaires
Security Questionnaires

Stealth Worker
Information Security (Cyber Security), Compliance and Privacy (GDPR &…
Cyber Security

Skypher
Cybersecurity compliance cockpit
Vulnerability Scanning

Riot
Cybersecurity awareness for fast growing companies
Security Awareness Training

Telivy
Automate your cyber security risk assessments
Cybersecurity Risk Assessment

Fuzzbuzz
Fuzzing as a Service
Fuzz Testing

Wolfia
Fill security questionnaires 10x faster with AI
Security Questionnaires

EdgeBit
Security platform to prevent useless supply chain investigation
Supply Chain Security
HTCD
Elevate your cloud security team with an AI workforce.
AI-Powered Threat Hunting
LotusEye
Detect anomalies in time series data with AI-powered analysis.
Anomaly Detection

Escape
Business Logic Security Testing for Developers & Security Teams
Business Logic Vulnerability Testing
Splunk
Gain real-time insights and accelerate your organization's resilience.
Log Management
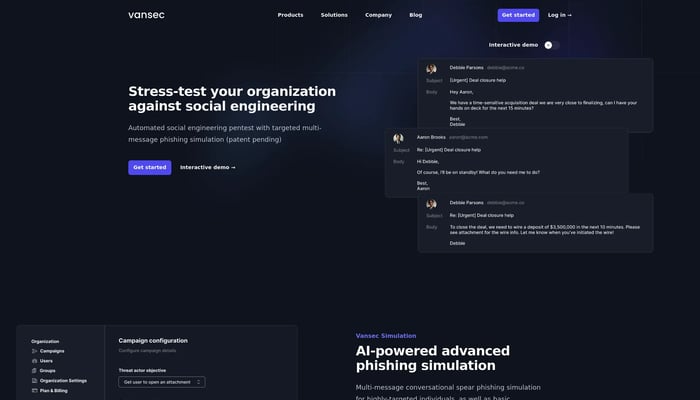

Vansec
Spear phishing simulation & security training platform
Spear Phishing Simulation

Agency
Advanced Personal Cybersecurity for Enterprises
AI-Powered Threat Detection
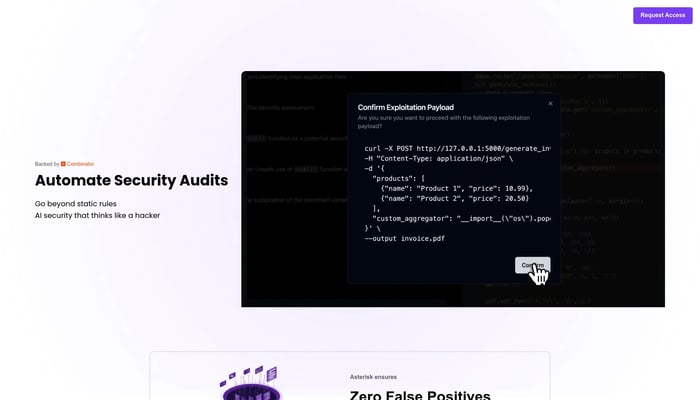

Asterisk
AI-augmented security audits for modern development teams.
AI-Powered Security Audits

HoundDog.ai Static Code Scanner
Proactively Prevent PII Leaks & Data Breaches
PII Data Leakage Detection

Gecko Security
Find, Fix, and Verify Vulnerabilities with AI
AI Vulnerability Detection
Peneterrer
Penetrate test your website using AI.
AI-Powered Penetration Testing

ContraForce
Hyperautomated Incident Remediation Platform
Incident Response Automation

