Categories
Data Breach Analysis Related Products
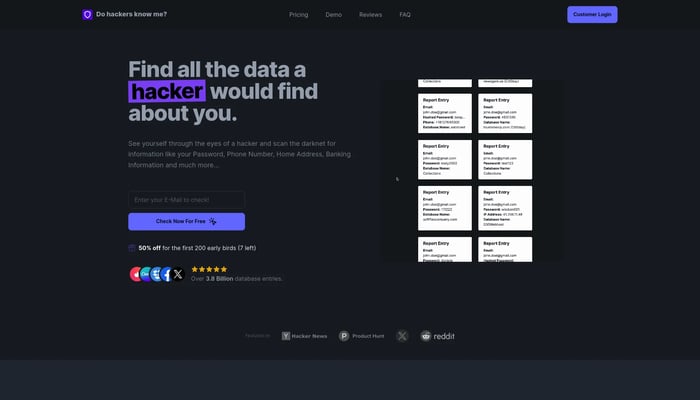
Do hackers know me?
See yourself through the eyes of a hacker
Data Breach Analysis

Overwatch
Enterprise software for strategic, risk, and cyber fraud intelligence
Fraud Detection
My Hacker News
Your daily dose of personalized Hacker News Newsletter.
Personalized News Digest

HoundDog.ai Static Code Scanner
Proactively Prevent PII Leaks & Data Breaches
PII Data Leakage Detection

Stealth Worker
Information Security (Cyber Security), Compliance and Privacy (GDPR &…
Cyber Security
LotusEye
Detect anomalies in time series data with AI-powered analysis.
Anomaly Detection
G-71 Security
Investigate leaks of text data
Text Data Leak Detection

Exploit Alarm
Vulnerability intelligence for real-time threat analysis
Threat Intelligence

HackGATE
Empowering ethical hacking with visibility and control
Penetration Testing

Cyber Pulse
Stay ahead of cyber threats with AI-powered intelligence.
Ransomware Intelligence

Remy
Resolve product security risks early with AI
AI-Powered Security

Escape
Business Logic Security Testing for Developers & Security Teams
Business Logic Vulnerability Testing

Metaplane
Data observability for modern data teams
Data Quality Monitoring
Splunk
Gain real-time insights and accelerate your organization's resilience.
Log Management

Stacksi
Automated Answers to Security Questionnaires
Security Questionnaires


Strac
Remove PCI, PHI, PII Leaks from SaaS, Cloud, Endpoints & Generative AI
SaaS Data Security

Securelog
Prevent data breaches by automatically finding and removing leaked secrets.
Secret Scanning

Telmai
Data quality profiling and monitoring
Data Profiling

Vuxep
Know where your data is leaked and which passwords to change
Dark Web Crawling


Lariat Data
Observability for Data Engineering Teams
Data Observability

Skypher
Cybersecurity compliance cockpit
Vulnerability Scanning

JumpWire
Dynamic access controls for all data and databases
Data Access Control

Dyneti Technologies
Reduce payment fraud
Payment Fraud Detection

Honeydew
The home for shared data logic
Data Validation

Oneleet
Automated security and compliance without security theater
Vulnerability Management

Tarsal
Data pipeline for your security data lake.
Security Data Lake

dataxreports.com
Browse our ready-to-use Google Data Studio templates
Data Studio Templates

TrueVault
We make Privacy Software for SMBs.
Data Privacy Compliance

Cyble
Cyble is one of the fastest-growing threat intelligence provider.
Data Analysis

Elementary
Open-source data observability for data teams
Data Quality Monitoring

