Categories
Encrypted VPN Related Products
Matrix
Secure, decentralized communication for individuals and communities.
Secure Communication

Element
Secure and sovereign communication, powered by an open standard.
End-to-End Encryption
Secure Share
Your Free B2B File Sharing Hub
Secure File Transfer
Securly
Web Filtering

PrimeVault
Supercharged custody, trading, and risk infra for institutional CeDeFi
Crypto Wallet Infrastructure

MedCrypt
MedCrypt gives medical device vendors cybersecurity features in a few…
Medical Device Security

TextBin
A privacy focused open source alternative to paste bin
Text Sharing
Threema
Private communication for individuals and businesses.
End-to-End Encryption

Teleport
The easiest, most secure way to access all your infrastructure
Secure Access

JumpWire
Dynamic access controls for all data and databases
Data Access Control
Signal
Private, secure communication with no compromise.
End-to-End Encryption

Layerup
Security Suite for LLMs
LLM Security

Protocol Labs
Protocol Labs makes internet protocols: IPFS, Filecoin, and more.
IPFS

Lava Lamps as a Service
Unpredictable randomness for robust security applications.
Cryptographically Secure PRNG
Elavon
Seamless payment processing solutions for businesses of all sizes.
Card Machines


Peer5
P2P delivery network that enables high quality video streaming
P2P CDN

Request Network
Request is a payment request technology & an ecosystem of apps
Crypto Invoicing

Safepay
Digital payments for businesses in Pakistan
Online Payment Gateway

Stealth Worker
Information Security (Cyber Security), Compliance and Privacy (GDPR &…
Cyber Security
Auth0
Securely manage access and identities for any application.
Single Sign-On

PropelAuth
Team-based authentication for B2B SaaS
User Management

Clad
Software to build the internet faster.
Subcontractor Management

ProxiedMail
Email forwarding with unlimited mailboxes
Email Forwarding

Mattermost
Secure Collaboration for Technical Teams
Secure Communication

Polarsteps
Easily plan, track, and relive your travels
Trip Itinerary

TrueVault
We make Privacy Software for SMBs.
Data Privacy Compliance

Doppler
The first SecretOps Platform.
Environment Variables

Pactima
Live video signing for real-time agreements
Live Video Signing

Passkey Ready
Find out if your users are ready for passkeys
Passkey Compatibility
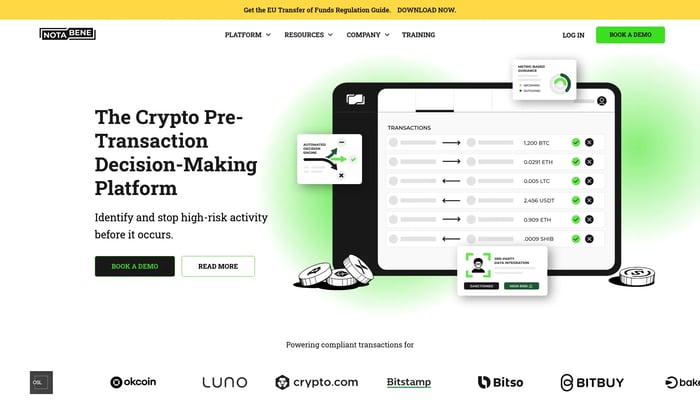

Notabene
Software to manage risk in crypto transactions
Crypto Transactions

