Categories
Verifiable Computing Related Products
Matrix
Secure, decentralized communication for individuals and communities.
Secure Communication


keyval
Open-source codeless monitoring pipeline
Codeless Monitoring

SiLogy
A collaborative test and debug platform for chip developers
Chip Simulation

Cinder
Operating system for trust and safety
AI Risk Mitigation
Veklar
The free, human social network
Privacy Focused

Hadrius
The Financial Compliance Copilot
Financial Compliance Automation

Honeydew
The home for shared data logic
Data Validation
Vexa
Real-time AI assistant for flawless business meetings.
AI Meeting Transcription

Democracy Earth
Censorship resistant democracies.
Blockchain Governance

CloudCheck
Optimize your cloud, minimize your costs
Cloud Cost Optimization

Hiro Systems
Hiro Systems build developer tools for Bitcoin L1 and the Stacks L2
Bitcoin Tools

HUMN-1
Human Content Certification
Human Content Detection

Axiom.ai
No-code Browser RPA
No-Code RPA

LLMWare
Build and Deploy Secure AI Solutions Locally for Regulatory Compliance
LLM for Finance
Vercel
Deploy faster, scale globally, and build the best web experiences.
Serverless Functions

Arva AI
AI agents to automate financial compliance
KYB Automation

Credal.ai
The safest way to use AI at the enterprise
Data Protection for AI

Welcome Onchain
Your web3 hub for companies, projects, and bounties
DeFi Project Information
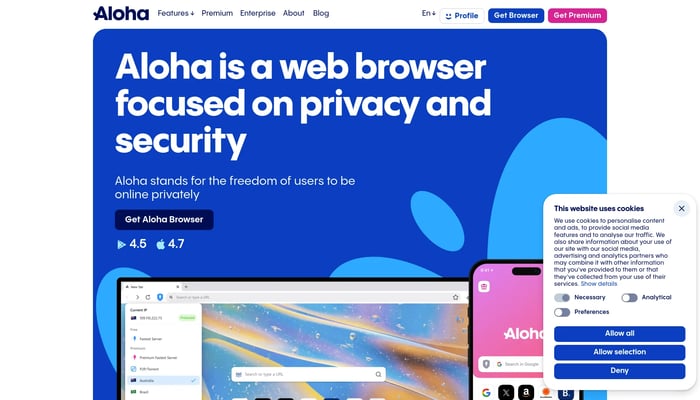

Private AI Assistant
True anonymity preventing queries from being 'fingerprinted'
Privacy-Focused AI
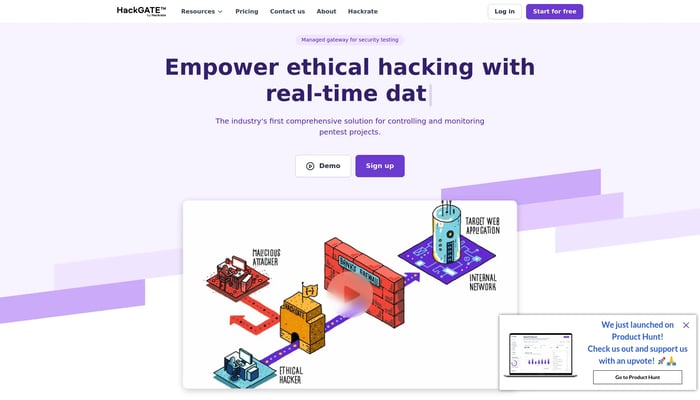

HackGATE
Empowering ethical hacking with visibility and control
Penetration Testing
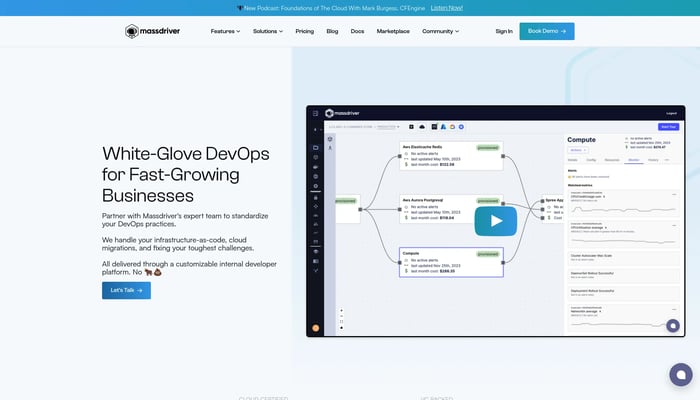

Massdriver
Deploy secure, scalable cloud infrastructure in minutes not days
Kubernetes

Transluce
Building a future where AI is understood, trusted, and accessible.
AI Explainability
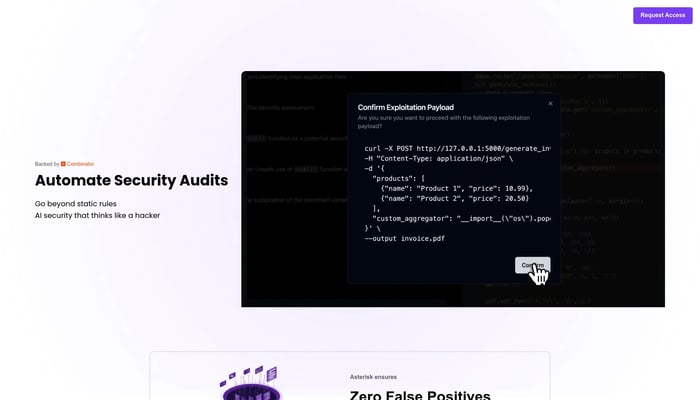

Asterisk
AI-augmented security audits for modern development teams.
AI-Powered Security Audits

TRM Labs
TRM is building a safer financial system for billions of people.
Fraud Detection

Accredible
Digital credentials to recognize achievement
Credential Management

Mattermost
Secure Collaboration for Technical Teams
Secure Communication
Qypt AI
Unlock a New Era of Confidentiality and Collaboration on the Go!
Secure Collaboration
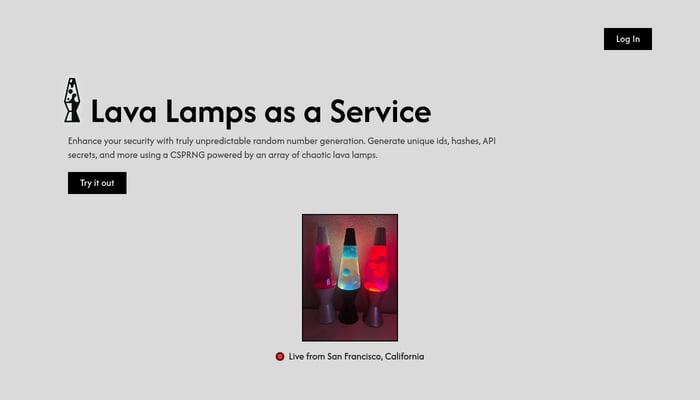

Lava Lamps as a Service
Unpredictable randomness for robust security applications.
Cryptographically Secure PRNG

Venu AI
Build your community with Venu AI
Community Building

Zelos Cloud
The First Cloud Platform for Firmware Development and Testing
Microcontroller Emulation

